MANAGED
aiSIEM
Disruptive Analytics, Holistic Security with aiSIEM.
Advanced Threat Detection and Remediation
Protecting all your digital assets, people and network round-the-clock at a fraction of the cost.
Real time advanced threat detection and auto-remediation with Machine Learning and Artificial Intelligence.
Stop the breach and keep business continuity at affordable cost!

The Problem with Traditional SIEM Solutions……
- Correlation rules are mostly generic – results in high percentage of false positives and negative.
- Heavy reliance on Static Data (event logs) – misses out key indicators of compromise for early threat detection and response.
- Behavioral Analytics with user identity, network flow and applications are absent – resulting in half-baked alerts with incomplete context.
- Threat Intelligence data is not considered for analysis enrichment – previously undetected malware will remain evasive.
aiSIEM takes a radically different approach to cybersecurity, ensuring pitfalls of traditional SIEM are averted while empowering enterprises to take on the challenges posed by emerging threat vectors, techniques and tactics.
Continuous Compliance – On Demand and At Scale
Stay current and stay informed with regulatory compliance check and balances all the time, even as your business grows with users, assets and digital footprint.
Operational Efficiencies in Threat Detection
Drastically reduce operational hassles with optimized analytics and automation to arrive at only the alerts that matter – eliminate false positives.
Qualitatively Enhanced Outcome
Find assurances from alerts backed by validated Indicators of Compromise (IOCs) and immediate manual or automated response.
Catch and neutralize known and unknown threats across your digital assets – on-premise, cloud or remote, before they turn into major incidents.
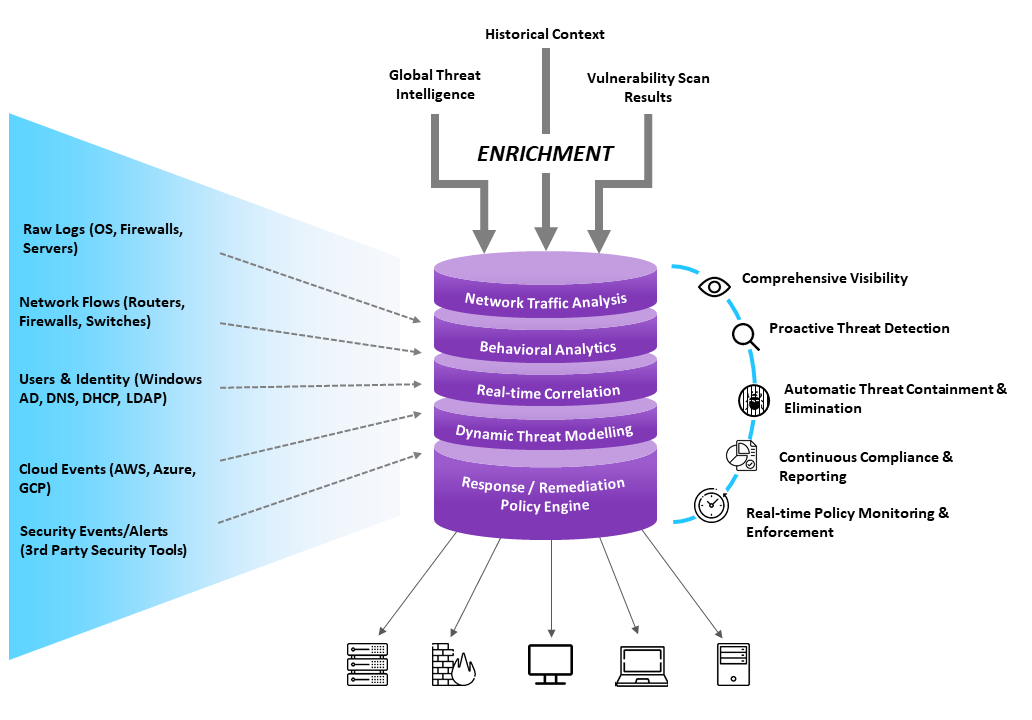
Sound security posture requires comprehensive visibility into cyber threats, exploits and attacks targeting your IT assets. aiSIEM stitches together validated list of threat indicators, correlated events and network traffic flows, enriched with threat intelligence, behavioral anomalies, historical context and vulnerability scan results. The outcome is highly effective and cohesive alerts without any fatigue and timely semi-automated or automated quick response.
Respond Fast. Limit Damage. Manage Risk.
Ingestion of Events, Logs, Flows and User Activity Data
from almost all sources; identities, networks, endpoints, clouds, and applications.
Contextual Enrichment
With threat intelligence (40+ sources) combines with vulnerability assessments and historical data.
Behavior Baselining and Profiling
For anomaly detection leveraging Machine Learning and Artificial Intelligence techniques
Advanced Event Correlation
(on-prem and cloud)
Behavioral patterns with Al and Dynamic Threat Models.
Identification of Threats
Based on rules-based policy creation, enforcement and notification for appropriate action and governance
Protection and Response
Based on automated remediation (based on incident triaging and or prebuilt playbooks) and real-time remediation.
Continuous Compliance and Reporting
Across several key areas – security, compliance, operations and investigations.
USE CASES