End-to-End Cybersecurity with aiXDR
Stay Vigilant, Stay Ahead of Your Adversaries.
When it comes to safeguarding digital information, IT assets and business data, IT organizations often contend with quasi-normal state, forced by the lack of deep composite insights from endpoints, servers, firewalls, users, entity behaviors, network traffic, vulnerabilities and threat intelligence.
Secure your final frontiers – whether in the remote workplace, in the cloud, in the office or in transit – with aiXDR.
Draw upon insights rendered by razor-sharp analytics, guided by AI and ML.

aiXDR takes a holistic approach to cybersecurity by gathering deep insights from endpoints, servers, clouds, network devices, applications, IOT, and OT and applying user identity, threat intelligence, and vulnerability assessment to establish threat profiles, generate threat indicators, raise essential alerts, and offer remediation path – automated or triaged.
In essence, the platform ensures multi-layered threat detection and response, relying on EDR, Network Behavior, Advanced Correlation (SIEM), Network Traffic Analysis, UEBA (ML-based), and SOAR for an All- In-One platform that is organically and seamlessly fused together.
- Endpoint Security with agent-based and agentless technology for Windows, macOS, and Linux OS
- Behavior baselining with applied Machine Learning for users and entities based on host-centric insights (services, processes, file access, telemetry, etc) and network flows
- Data Exfiltration (breach), Insider Threat and DDoS Attack detection with network traffic pattern analysis
- Exhaustive reporting across several key areas – security, compliance, operations, and investigation
- Rules-based policy creation, enforcement, and notification for appropriate action and governance
Merely relying on any particular layered protection like EDR, IDS/IPS, SIEM, SOAR or Network Security will not provide adequate coverage for the critical assets that your business relies on.
aiXDR is a fusion of all these protective layers built organically with the speed of real-time analytics, defense in-depth oversight and dynamically adaptive threat models guided by Artificial Intelligence.
Advanced Security for Endpoints and Networks
Block brute-force attacks on endpoints leading to compromised credentials, VPN, early detection of malware and ransomware, network based attacks, and ultimately protect your users, data, applications, infrastructure and systems.
Real-time AI/ML Based Detection and Response
Benefit from security automation through Machine Learning for anomaly detection and Artificial Intelligence for Dynamic Threat Modeling (DTM) as accurate risks are quantified based on threat indicators. Stop threats and limit blast
zones before they turn into major incidents.
Instant 24/7 Response
Enable instant responses to governance policy violations through user-defined controls and initiate automated remediation to threats with high severity and confidence level, targeted at business-critical assets.
MITRE ATT&CK Modelling
Leverage MITRE ATT&CK Tactics, Techniques and Procedures to model actual intrusions and attacks, focusing on kill chain activities such as reconnaissance, beaconing, evasion, privilege escalation, lateral movement and exfiltration.
Single Pane of Glass
Rest assured with total protection against cyber security threats, exploits and attacks across your servers, endpoints and applications in the Cloud, On-Premise, Edge (IIoT & IT-OT) and Remote Workplaces.
Complete Attack Surface Visualization
Monitoring your IT assets 24×7 with full details of behavioral attributes, prioritized statistics, performance indicators, drill-down datapoints and consolidated reports – visual and tabular – ensuring rapid attack/breach detection,
regulatory compliance, threat hunting, operational oversight, and executive summary.
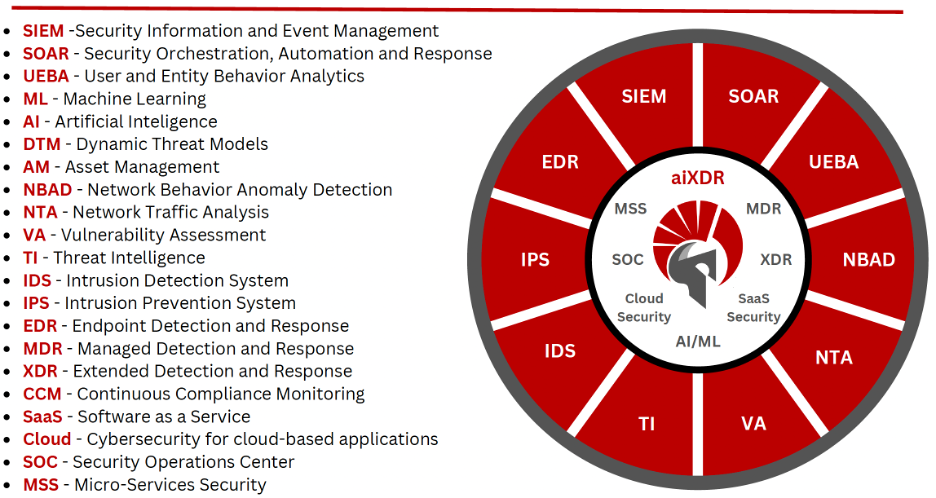
Built from the ground up with NATIVELY integrated capabilities of the components from the SOC visibility triad.
Three core elements of the SOC visibility triad:
- SIEM/UEBA provides the ability to collect and analyze logs generated by the IT infrastructure, applications and other security tools.
- Endpoint detection and response provides the ability to capture execution, local connections, system changes, memory activities and other operations from endpoints.
- Network-centric detection and response (NTA, NBAD and IDS/IPS) is provided by the tools focused on capturing and/or analyzing network traffic.
By combining the data from SIEM, EDR, and NDR, our security teams can get a comprehensive view of your environment and identify threats more quickly and efficiently, helping reduce the risk of a successful cyberattack.
Goliath Cyber – aiXDR Platform
Offered as a SINGLE license platform, with every component contained in the image below!
USE CASES

Malware Detection

Brute Force Attacks
Traffic Anomaly Detection

Insider Threat
Vulnerability Exploits

