Trident – A Data & Risk Management Program that provides a complete cyber risk management and compliance program in a single, unified service. Capabilities include internal and external vulnerability scanning, data sensitivity scanning, compliance assessment, secure configuration assessment, dark web monitoring, risk monetization, and more!
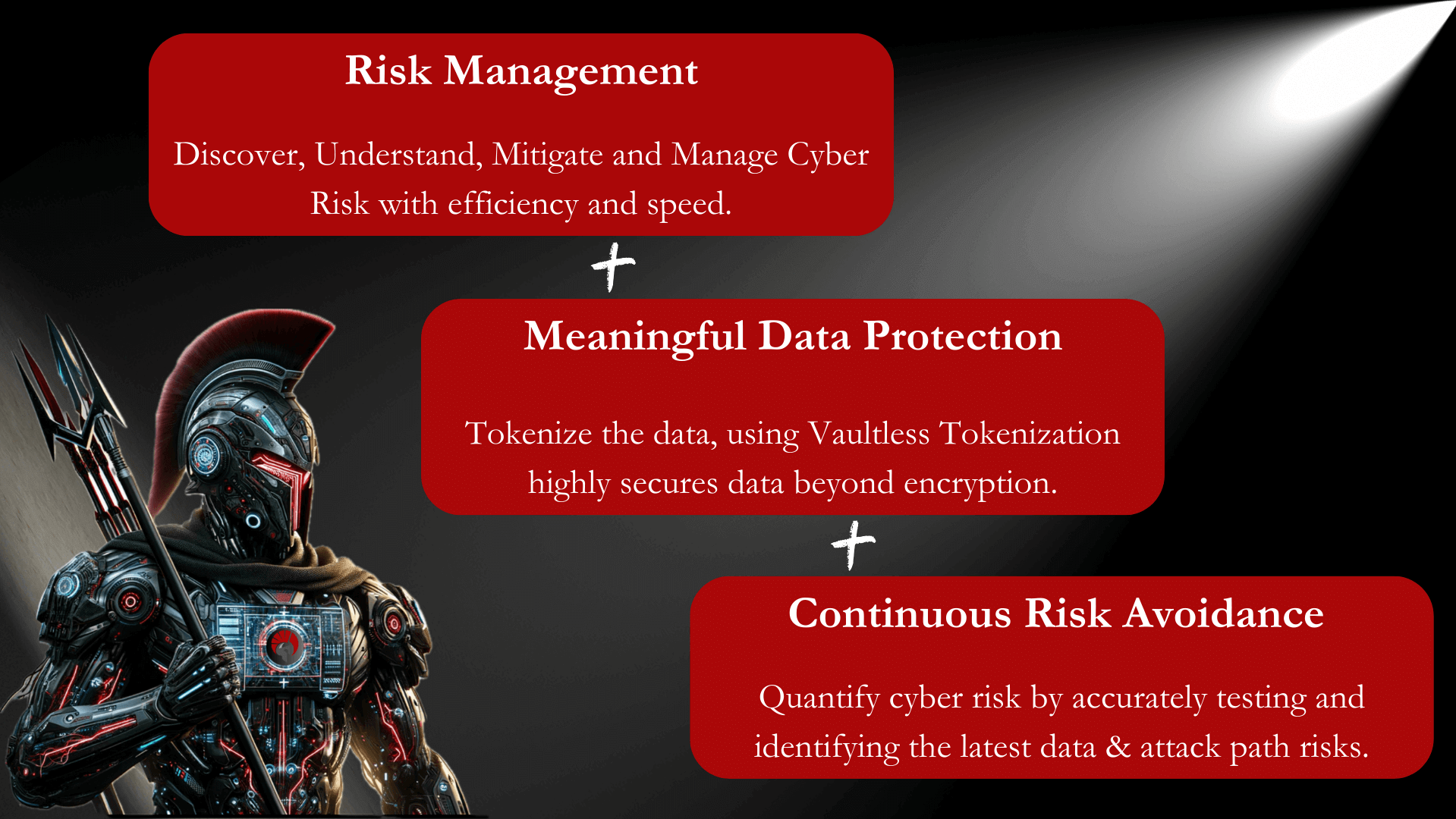
Discover, Understand, Mitigate and Manage your cyber risk, and manage compliance, without the need for a bloated tool stack.
Reduce cyber risk in a holistic, cost-effective manner while simplifying operations.
PROGRAM FEATURES
Data Sensitivity Scanning to find and protect sensitive data on-prem and in cloud environments, including Microsoft 365 and Google Workspace…
Data Sensitivity Scanning capability allows security teams to conduct quick scans on selected devices to find any sensitive data stored on them that needs to be protected. This includes data stored either on-prem or on the cloud, with scanning options available for Microsoft 365 Exchange mailboxes, SharePoint data, OneDrive servers, and Active Directory; and Google Workspace apps like Google Drive, Gmail, and more. The data can then be graded and classified based on volume, type, and business impact, and either deleted or encrypted/tokenized to protect against breaches and ransomware attacks. Popular search categories include passwords, bank account details, SSNs, credit card data, and Driver’s Licenses.
Goliath Cyber finds where your sensitive data is located and helps take the proper measures to protect it before it gets into the wrong hands.
Beyond Encryption…
Vaultless Data Tokenization replaces sensitive data with random tokens, ensuring no third-party data storage and reducing data breach risks.
Detect and mitigate security vulnerabilities before they can be exploited. Deploy patches from within the platform…
Vulnerability management covers the complete cycle of discovering, classifying, analyzing and mitigating security vulnerabilities in an organization’s IT environment, with the end goal of closing security gaps and reducing cyber risk. In a constantly evolving digital landscape, new vulnerabilities and threats emerge every day. Threat actors have been known to start exploiting new vulnerabilities within hours of their publication by vendors. This means that for a vulnerability management program to be really successful, scanning for vulnerabilities needs to be an ongoing process so new threats can be found and removed before they can be exploited by cybercriminals.
With options to run both internal and external scans. Scans can be scheduled as per your convenience, with the option to set up daily scans. Users can also apply Windows patches, and patch third-party Windows-based applications from within the platform.
Complete visibility into the vulnerabilities in network-connected devices, systems and web applications, and allows them to easily triage these vulnerabilities based on severity levels, create mitigation plans, and patch systems quickly.
Secure Baseline scanning to identify and fix configuration weaknesses in operating systems…
Secure baseline scans are designed to find configuration gaps and security weaknesses in operating systems, using specific security frameworks as comparison benchmarks. Security teams can perform these scans to compare different OS configuration settings against the baseline controls recommended by security frameworks, and make the changes necessary to harden configuration and reduce their organizations’ attack surface. Along with configuration hardening for improved security, secure configuration assessments also help organizations meet the compliance requirements relevant to their industries.
Using the Center for Internet Security’s (CIS) Benchmarks and DISA’s Secure Technical Implementation Guides (STIGs) as the benchmarks for secure configuration scanning to protect both commercial and government entities against breaches. The systems being scanned are put through hundreds of tests under different policy categories and assigned performance grades based on the test results. Scan results include detailed recommendations to fix misconfigurations and close security gaps, and the functionality to create and execute mitigation plans from within the platform.
Find out if any of your organizations’ data is being discussed in underground hacker forums…
Dark web monitoring refers to tracking an organization’s information on the dark web (hacker forums, unindexed online activity by threat groups, etc) to check if any of its sensitive data has been compromised or is being sold illegally or discussed in hacker forums. Actively tracking your organization’s IPs, domains and email addresses on the dark web can help you predict and prevent serious attacks, be alerted to breaches early so you can initiate incident response, or assess damage more accurately if a breach has already occurred.
With the dark web monitoring tool, you can find any of your sensitive information being discussed in criminal forums, underground sites, and the untracked/hidden parts of the internet that you can’t find using search engines. Our dark web crawler combs the dark web to find any compromised accounts associated with your domains, and whether your data or brand is being discussed or sold in hacker marketplaces. Dark web intelligence helps you spot signs of potential attacks against your organization early, so you can take preventive measures to strengthen your defenses and stop malicious activity before it causes serious damage.
Get an estimate of the financial impact of cyber incidents or attacks in monetary terms…
Cyber Risk Monetization involves estimating the financial impact of different kinds of cyber incidents and attacks on an organization based on its risk levels, and expressing this in monetary terms. By putting a dollar amount against specific incident types, risk monetization helps security teams make informed cybersecurity decisions, in addition to getting the leadership’s buy-in on security investments. With a clear idea of how much a breach or a ransomware attack could cost their organization, C-level executives become more open to supporting strategies for reducing cyber risk.
The Risk Monetization feature gives you an estimate of the financial impact of a potential data breach or ransomware attack based on the value of your data and infrastructure assets, and a per record breakdown of sensitive datasets. The platform also gives you an estimate of residual risk in dollars, and what you can do to reduce this.
With attack impact presented in specific dollar amounts, you are much better placed to get leadership buy-in on increasing security investment than if you talked in technical terms alone.
Cyber Risk Mitigation and Progress Tracking…
Risk Mitigation involves taking the appropriate measures to fix security weaknesses and vulnerabilities in enterprise systems, following the vulnerability assessment process.
We understand that establishing accountability is critical to the success of any risk mitigation plan, so we’ve made it easy for users to create mitigation plans, set due dates and assign specific mitigation tasks to team members based on scan results. Mitigation tasks can be assigned to either IT and InfoSec team members or to actual end users in departments such as HR, finance, etc. Each assigned mitigation task is given a start and finish date to hold people and organizations accountable.
The goal, as with other risk management processes, is to reduce cyber risk and with mitigation plans in place, bring the organization’s attention to the risks identified and the steps being taken to handle those risks.
Generate consolidated security scorecards to share with leadership and other stakeholders…
Security Score Cards take the information collected by the latest scans of your IT environment and assets, and present it on a single, unified dashboard. You get a complete view of the entire organization’s cyber risk and internal & external attack surface, which can be easily presented to leadership teams or business stakeholders to give them a clear understanding of the company’s security posture. The score cards will also help you demonstrate progress and how quickly you were able to move the needle in the direction of reducing tactical cyber security risks.
With a unified view of risks and vulnerabilities across your databases, servers, endpoints, applications and computing environments, you can help your organization to understand their security gaps and weaknesses, and which operational areas to focus on in order to attain cybersecurity maturity.
Follow a few easy steps to create assessment reports in minutes…
Information Security teams are constantly battling against time to stay ahead of threat actors. The risk management platform gives you the ability to perform Cyber Risk assessments and create assessment reports in minutes by following 10 simple steps. With vulnerability scans, assessments and reporting done in a matter of minutes, security teams can find and remediate vulnerabilities before a cybercriminal has a chance to exploit them.
Our assessment reports collate the key findings under all scan categories and features in the platform – External/Internal Vulnerability Assessment, Data Sensitivity Scanning, External Web App Testing, Secure Configuration, Dark Web monitoring and Risk Monetization – to provide a complete picture of the security gaps in your organization’s IT environment. Monetizing risk is key when showing the leadership team or business stakeholders where the focus needs to be to reduce risk, and to get budget-holders on board for future funding to strengthen security.
Assess compliance with multiple frameworks and privacy standards including ISO 27001, NIST 800-53, HIPAA, PCI DSS, the CIS Controls, and more…
Compliance with cybersecurity standards and regulatory frameworks can be complex. Data privacy requirements vary based on industry sector and country, and many organizations need to demonstrate compliance with multiple frameworks to meet legal obligations. GRC and Compliance Assessment features enable organizations to track and assess compliance with multiple frameworks and data privacy regulations.
The platform includes a complete suite of GRC functions for the following: ISO/IEC 27001, NIST 800-53, HIPAA, PCI DSS, CIS Critical Controls v8, NIST Cybersecurity Framework, NIST 800-171, the ACSC’s Essential Eight, the UK’s Cyber Essentials, and CyberSecure Canada. It also gives you the ability to perform Microsoft Copilot Readiness Assessments to ensure secure deployment and manage the data consumed and generated by Copilot more effectively.
Review the compliance status, gaps and pending tasks for all frameworks in a single, unified dashboard before diving deeper into detailed assessment.
Quantify cyber risk by continuous, accurately testing and identifying the latest attack paths. Built for continual use, enabling notification against proven actual attack paths.
